In today’s complex world, safeguarding your assets, personnel, and sensitive information isn’t just a good idea; it’s an absolute necessity. Whether you’re running a small business, managing a large corporation, or overseeing a critical infrastructure site, understanding the vulnerabilities in your physical environment is the first step toward building a robust security posture. It’s about proactively identifying weaknesses before they can be exploited.
This proactive approach often involves a thorough physical security assessment. This isn’t just a casual walk-through; it’s a systematic examination of your facility’s defenses, from the perimeter fences to the locks on your server room doors. The goal is to get a clear, unbiased picture of where you stand, what risks you face, and what improvements are needed to enhance your overall protection.
Once an assessment is completed, the findings, observations, and recommendations need to be presented in a clear, organized, and actionable manner. This is where a well-structured physical security assessment report template becomes incredibly valuable. It transforms raw data into an understandable narrative, guiding decision-makers toward informed security enhancements.
What Goes Into an Effective Physical Security Assessment Report?
Creating a comprehensive and actionable report after a physical security assessment is crucial. It’s the document that communicates the findings, justifies recommendations, and often serves as a roadmap for future security investments. Without a structured approach, the assessment’s insights can be lost in disorganized notes or unclear explanations. A good report goes beyond simply listing problems; it analyzes them within the context of an organization’s operations and provides practical, prioritized solutions. It acts as a bridge between the technical security expert and the management team responsible for implementing changes.
Executive Summary
This is arguably the most critical section for busy executives. It provides a high-level overview of the entire assessment, summarizing the key findings, major risks identified, and the most critical recommendations. It should be concise, impactful, and written in a way that allows the reader to grasp the essence of the report without delving into every detail. Think of it as a snapshot that captures the core message and the most urgent action items.
Scope and Methodology
Before diving into findings, it’s important to clearly define what was assessed and how. This section outlines the boundaries of the assessment (e.g., specific buildings, areas, or systems included or excluded) and describes the methods used (e.g., site visits, interviews, document reviews, vulnerability scanning, penetration testing). Establishing the scope and methodology provides context for the findings and ensures transparency in the assessment process.
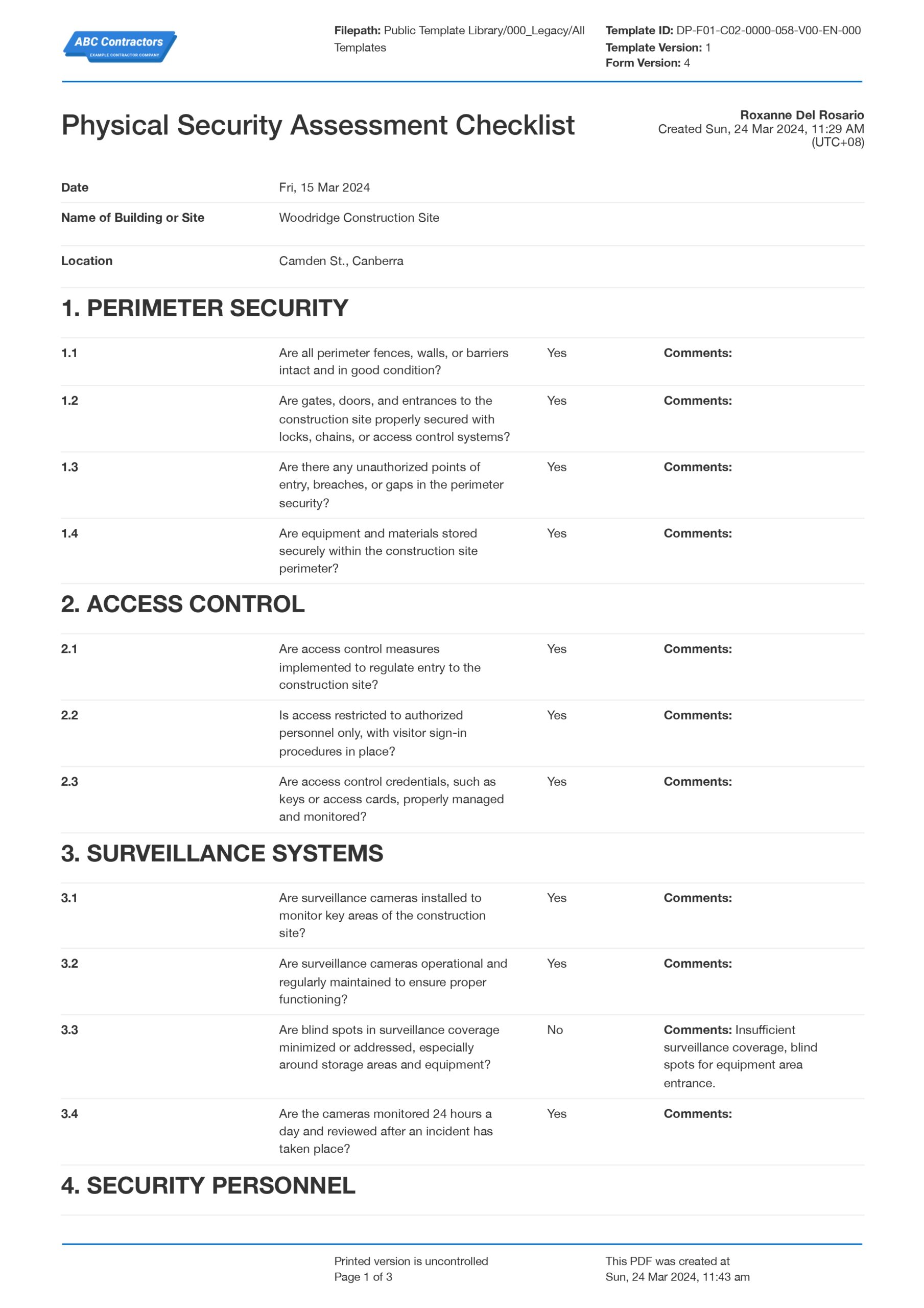
Findings and Observations
This is the heart of the report, detailing all the security strengths and, more importantly, the weaknesses identified during the assessment. Findings should be presented clearly and objectively, often supported by evidence such as photographs, diagrams, or specific examples. This section typically covers various aspects of physical security, including perimeter security (fences, gates, lighting), access control systems (keys, cards, biometrics), surveillance (CCTV, monitoring), intrusion detection, personnel security, and security policies and procedures. Each observation should be fact-based, avoiding speculative language.
Risk Analysis
Simply identifying a weakness isn’t enough; the report must also articulate the potential impact of that weakness. The risk analysis section evaluates each finding in terms of its likelihood of occurrence and its potential impact on the organization’s assets, operations, and reputation. Risks are often categorized (e.g., high, medium, low) to help prioritize remediation efforts. This analytical step transforms observations into meaningful insights for decision-makers.
Recommendations
Following the findings and risk analysis, this section proposes specific, actionable solutions to mitigate the identified risks. Recommendations should be practical, clear, and ideally, provide estimated costs or resource requirements where possible. They should be prioritized based on the severity of the associated risks, allowing the organization to address the most critical vulnerabilities first. Examples might include upgrading locks, installing additional cameras, implementing new access control policies, or conducting staff training.
Leveraging a Physical Security Assessment Report Template for Efficiency
Using a predefined physical security assessment report template brings a multitude of benefits, streamlining a process that can often be complex and time-consuming. Primarily, it ensures consistency across different assessments, whether they are conducted by the same individual over time or by various team members. This standardization means that reports will always cover the essential elements, making comparisons easier and ensuring no critical details are overlooked, which is vital for maintaining a comprehensive security posture across multiple sites or departments.
Furthermore, a well-designed template significantly boosts efficiency. Instead of starting from scratch with each new assessment, the template provides a ready-made structure, allowing assessors to focus their energy on gathering accurate data and formulating insightful recommendations rather than on report formatting. This not only saves valuable time but also reduces the likelihood of errors or omissions that can occur when building a report from the ground up, ensuring that every physical security assessment report template consistently delivers high-quality information.
Finally, templates enhance the clarity and professional presentation of the report. They guide the assessor to include all necessary information in a logical flow, making the final document easier for stakeholders to read, understand, and act upon. When a report is professionally organized and easy to digest, it increases the chances that its recommendations will be given the serious consideration they deserve, leading to more effective and timely security improvements.
The meticulous process of assessing and documenting physical security vulnerabilities is a cornerstone of effective risk management. A comprehensive report doesn’t just highlight problems; it empowers an organization to make informed decisions and strategically invest in solutions that truly fortify its defenses. It transforms abstract security concerns into concrete, manageable action items, fostering a safer and more secure environment for everyone involved.