In an increasingly complex world, recognizing and reporting unusual incidents has become a cornerstone of safety and security for individuals and organizations alike. From subtle anomalies in financial transactions to unexpected behaviors in a public space, what might seem like a minor irregularity could, in fact, be a critical piece of a larger puzzle, hinting at potential fraud, threats, or other harmful activities. The challenge often lies not just in spotting these deviations, but in documenting them in a clear, concise, and actionable manner.
Imagine trying to recall every detail of an event days or weeks later, or attempting to communicate its nuances to someone who wasn’t there. Without a structured approach, crucial information can be easily overlooked, details might be misremembered, and the overall effectiveness of your report could be significantly diminished. This lack of standardization can impede investigations, delay appropriate responses, and even compromise the security of an entire system or community.
This is precisely where a well-designed suspicious activity report template becomes indispensable. It serves as a vital tool, transforming the often-daunting task of reporting into a streamlined, systematic process. By providing a clear framework, it ensures that all necessary data is captured consistently, making it easier to share information, support investigations, and contribute to a safer environment for everyone involved.
Understanding the Importance of a Structured SAR
When an incident occurs that raises an eyebrow, the immediate reaction is often to describe it verbally, or jot down notes in a haphazard fashion. However, these informal methods frequently fall short, leading to incomplete records, subjective interpretations, and ultimately, reports that are difficult to act upon. Without specific categories for information like dates, times, locations, and involved parties, the narrative can become muddled, and critical facts might be missed entirely, leaving investigators with more questions than answers.
A structured approach, such as employing a dedicated suspicious activity report template, directly addresses these pitfalls. It acts as a guided checklist, prompting the reporter to consider and record every relevant detail in a standardized format. This consistency is invaluable because it minimizes ambiguity and ensures that all essential data points are covered, creating a comprehensive and reliable record that stands up to scrutiny. It transforms a scattered collection of observations into an organized, actionable document.
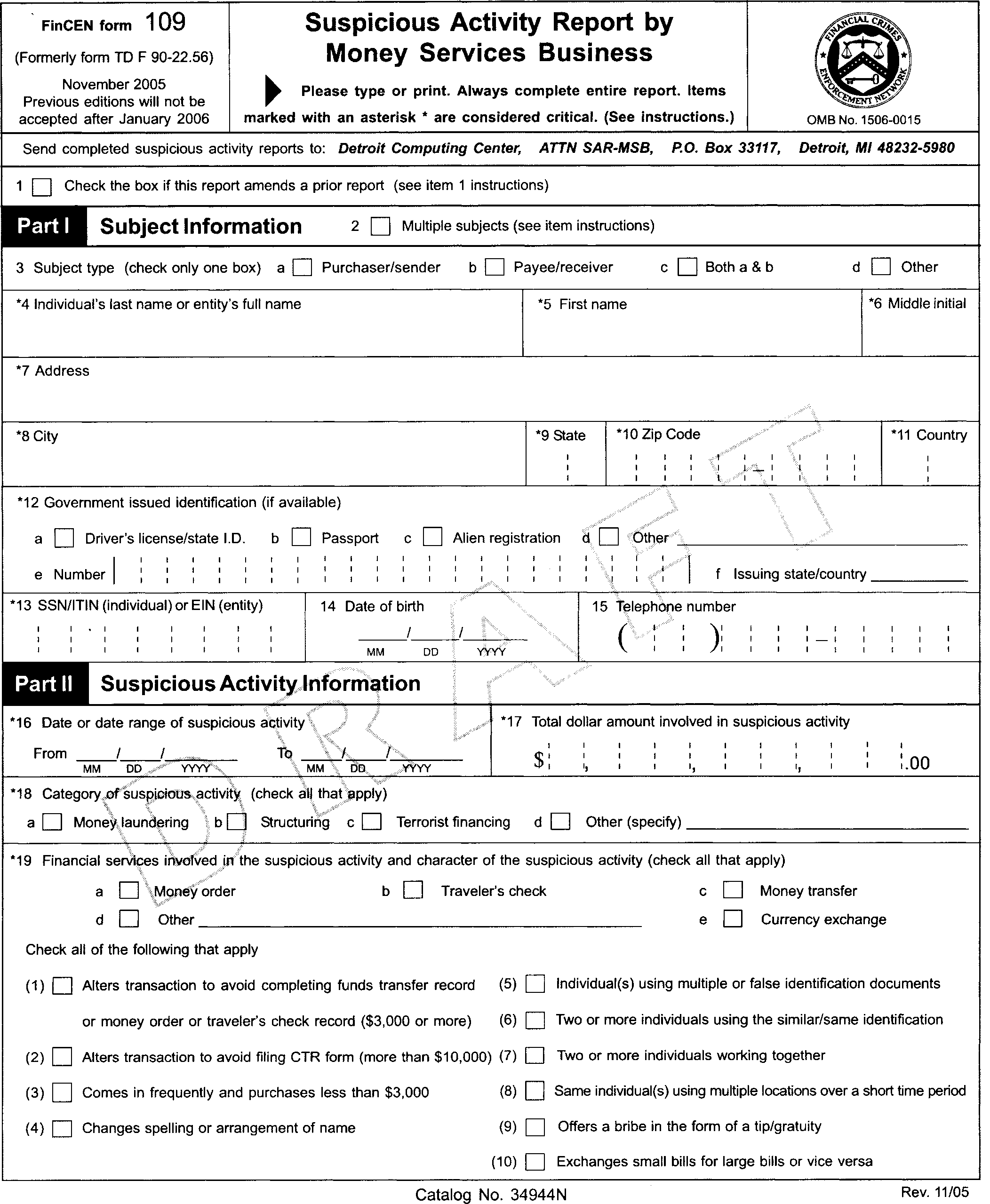
Furthermore, many industries are bound by stringent regulatory requirements concerning the reporting of suspicious activities. Financial institutions, for example, must adhere to anti-money laundering and counter-terrorist financing laws, which mandate specific information be included in their reports. A robust template is not just good practice; it is a compliance tool that helps organizations meet these legal obligations, avoiding potential penalties and reinforcing their commitment to ethical operations.
Beyond compliance, the operational efficiency gained from using a template is substantial. It significantly reduces the time and effort required to compile a report, as reporters don’t have to start from scratch each time. This efficiency extends to those who receive the reports as well, allowing them to quickly identify key information, assess the situation, and initiate appropriate actions or investigations without sifting through disorganized data.
Finally, consistent reporting through a standardized template empowers organizations to perform better analysis over time. By having uniformly structured data, it becomes possible to identify patterns, trends, and recurring threats that might otherwise go unnoticed. This aggregated intelligence can then be used to enhance security protocols, train staff more effectively, and proactively mitigate future risks, moving from reactive responses to preventative strategies.
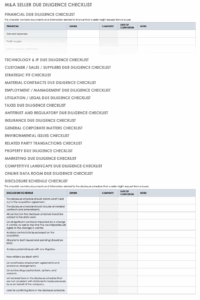
Key Elements of an Effective Suspicious Activity Report Template
- Date and Time of the Suspicious Activity: Pinpointing exactly when the event occurred.
- Location of the Activity: Specifying the precise address or area.
- Detailed Description of the Activity: A narrative explaining what was observed, including any specific actions, conversations, or objects.
- Individuals or Parties Involved: Names, physical descriptions, identifying features, or other relevant details of persons present.
- Assets Involved: Any accounts, vehicles, property, or other assets connected to the activity.
- Reporting Party Information: Details of the person submitting the report, for potential follow-up.
- Actions Taken: Any immediate steps taken by the reporter or security personnel.
- Witness Information: Details of anyone else who observed the activity.
Who Benefits from a Standardized Reporting Process?
The utility of a robust system for documenting unusual incidents extends far beyond the traditional boundaries of law enforcement or high-security environments. In today’s interconnected world, nearly every sector and organization faces some level of risk, whether it is related to financial malfeasance, physical security threats, or breaches of internal policies. Therefore, the ability to clearly articulate and record these concerns is a universal requirement for maintaining integrity and safety.
Various industries and roles can greatly enhance their security posture and operational efficiency by adopting a standardized reporting process. Financial institutions rely on it heavily for compliance with Anti-Money Laundering regulations. Retail businesses use it to track and investigate instances of theft, fraud, and employee misconduct. Educational institutions find it crucial for reporting bullying, potential safety threats, or unauthorized access. Even human resources departments can leverage it to document workplace harassment or policy violations, ensuring fair and consistent handling of sensitive situations.
Ultimately, a flexible suspicious activity report template serves as a foundational tool that can be adapted to suit diverse needs. While the core components of “who, what, where, when, why, and how” remain consistent, the specific details required might vary. This adaptability ensures that whether you are a bank teller flagging a dubious transaction or a school administrator noting unusual behavior, the underlying structure provides a consistent, reliable method for capturing critical information, making everyone a more effective contributor to collective security.
The proactive documentation of suspicious events is an empowering step for any individual or organization committed to safety and integrity. By adopting a structured approach, you ensure that every potential red flag is not just noticed, but properly recorded, becoming a valuable piece of data rather than a fleeting concern. This methodical process underpins more effective investigations, fosters a culture of vigilance, and significantly strengthens overall risk management.
Embracing a clear, comprehensive reporting mechanism offers invaluable peace of mind. It means that when unusual circumstances arise, you possess the tools to act responsibly and effectively, contributing to a more secure environment for your community, your colleagues, or your clients. Having a reliable system in place demonstrates a commitment to safeguarding assets, people, and reputation, ultimately building trust and resilience against unexpected challenges.